With cyber risk gaining more attention following increased security breaches and a rise in remote working, a closely followed ESG rating system is adding new cyber questions to its scoring methodology. This could prompt companies to disclose more specifics on how they manage related risks.
The growth of environmental, social and governance (ESG)-focused investors and more robust corporate disclosure has spawned dozens of outside ratings that attempt to quantify how well companies are addressing ESG issues. One of the most visible ratings comes from the large and influential proxy advisory firm Institutional Shareholder Services (ISS) with its QualityScore ratings. In the firm’s latest update to its methodology, ISS is adding cyber-related questions — a hot topic in the remote working environment.
QualityScore ratings are included for informational purposes in ISS’ annual research reports, which also contain voting recommendations to investors for annual shareholder meetings. While such ratings generally do not impact ISS’ actual voting recommendations, their visibility within the reports makes them a frequent topic of conversation within the boardroom. As such, when ISS publishes its annual methodology updates, companies typically look at their own disclosure to determine accuracy and whether there are certain disclosure enhancements that could be made to improve their QualityScore rating.
As with other areas of public disclosure, companies need to balance their desire for improved governance ratings with potential risks of over-disclosing on topics. This is especially true when you realize that the ISS governance ratings do not directly impact actual proxy voting recommendations or outcomes. It’s also important to remember that changes in ESG ratings by agencies are not always, or even often, a reflection of the actual practices of the individual company. It’s often driven by intricate and evolving changes to methodologies.
“Companies should focus on managing their ESG risk and opportunities based on internal business needs while also balancing what competitors are doing on these items as well — as opposed to doing what a rating agency rates as best practice,” says Laura Wanlass, a partner in Aon’s human capital practice and global governance leader. Nonetheless, it’s important to track changes from ratings agencies and be aware of their potential implications and how to message outcomes of ratings scores to investors and other stakeholders as needed, she says.
Cyber-Related Questions for 2021
Starting this year, ISS includes several cyber-related questions in the ISS QualityScore updates, under the sub-categories of “Information Security Oversight” and “Information Security Risk Management Oversight.”
The table below shows the questions in which the firm is using to rate companies.
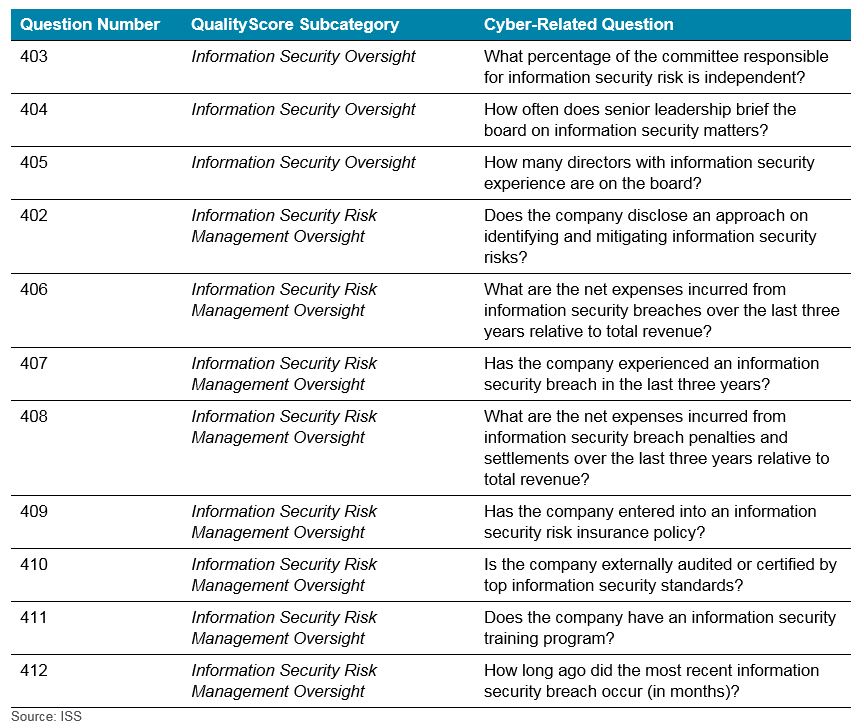
The questions under the Information Security Oversight subcategory are commonly disclosed in the proxy statement already (often under the board oversight risk section and board matrices/board skills and qualifications sections). However, the questions ISS is including under Information Security Risk Management Oversight are not only uncommon in the marketplace but could result in risks associated with disclosing sensitive information should it be included in publicly filed Form 10-K disclosures.
We reviewed 10-K disclosures at S&P 1500 companies that have filed a Form 10-K for the most recent fiscal year as of January 31, 2021. Key findings include:
- Most of the companies disclose their compliance with The California Consumer Privacy Act, General Data Protection Regulation and other Regional Cyber Regulations Act.
- Mostly the cyber-related risk is regulated by a specific board committee, often the audit committee.
- A majority of companies disclose their preventive measures to reduce risk related to cyber. However, fewer firms disclosed details about actual steps taken, such as implementing firewall, auto backups and anti-virus software.
- Some companies had a designated cyber risk position in leadership, with chief information or security officer being most prevalent.
- Some companies engaged with third parties, however there was no disclosure of the vendor name.
- Most companies maintain cyber insurance, however there was no disclosure of their coverage amount.
Risks of Disclosing Too Much
Our research finds that detailed disclosure surrounding cyber breaches and insurance coverage are uncommon. Public companies are balancing the need for transparency on their cyber-related practices — which can boost their ratings score and please ESG-savvy investors — with the risk of divulging vulnerable information on a firm’s cyber prevention plans.
The same challenge applies to third-party organizations. Organizations often fall short in identifying very specific risks based on their industry or sector, as well as assets that pose the most potential risk. For example, if you are a credit card processor, your largest risk is that your “vault” of credit card information is compromised. This would result in significant fines and fees from government entities, fees or sanctions from industry bodies, and significant reputational damage. A similar risk exists for hospital groups’ patient health records. Yet, most companies are very generic in their disclosure, even when there are opportunities to be more specific and relate risks back to the unique nature of a business’ operations.
“We are constantly taking questions from our clients about trying to find the right balance between what they need to disclose to give stakeholders comfort that they have sufficient controls in place, while not going so deep that it raises lots or questions or red flags. Companies have an opportunity to improve cyber disclosure by providing more specificity around risk mitigation efforts unique to their industry,” says Christopher J. Uriarte, chief information officer, Aon’s Cyber Solutions.
For more information about how we work with C-suite and boards on cyber risks and disclosure, please contact the authors or write to rewards-solutions@aon.com.